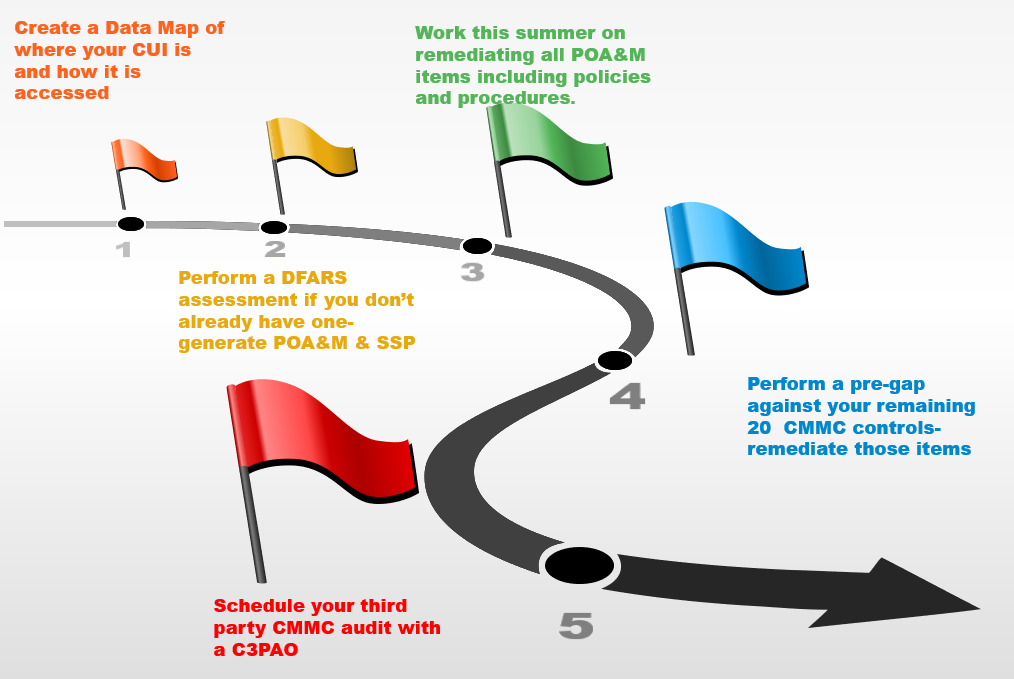
There has been much talk about the CMMC (Cybersecurity Maturity Model Certification) Program. Let’s take a minute to understand the levels of compliance that you may have to meet.
There are 17 Domains that are spread over 5 levels of the maturity categories.