In the last two years, we have seen technology has become the driving force for businesses. Whether it’s introducing remote working, or swapping your business practices to online. Technology has become a competing factor, and if your business isn’t prepared to accommodate these changes, you may get left in the dust behind your competitors.
Blog
The Bare Minimum Your Business Should Do To Protect Itself
Potential Threats To Your Network and IT Insfrastructure
What You Need To Know About Phishing Attacks

Phishing attacks have been a problem for many years, but they have become increasingly difficult to detect recently because of the rise of sophisticated phishing kits. These kits provide everything a cyber-criminal needs to set up a phishing site and send out mass emails to launch a spearphishing attack.
F1 Solutions: Be Alert Russia is on the War Path

Many of you woke up to the news that Russia has invaded Ukraine. I am not a political commentator so I will save that for the experts; however, this will have a real effect on our Cyber Security world moving forward. Let’s face it Russia and China have been equally involved in the drastic rise of cyber hacking in western countries over recent years.
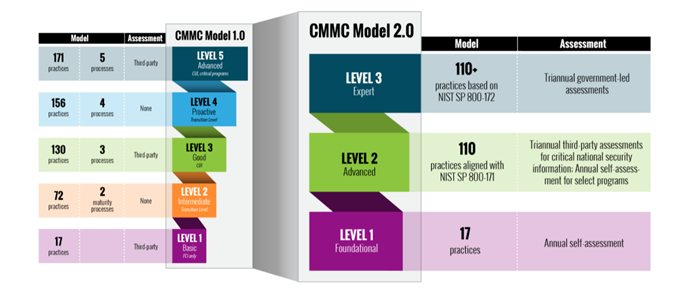
CMMC Newly Announce Changes

Here in summary are 3 new realities we must face in the next few years due to these new CMMC announcements:
Bifurcation Is Dead, Back to Third Party Audits
Last November when CMMC was drastically re-organized, we were introduced to the word “Bifurcation”. Who the heck knew what that was? After we all stopped to look it, we discovered that the DoD in conjunction with CMMC was going to divide out CUI into categories.
Tips For Making Your Network More Secure In 2022
Top 3 Managed IT Services You Need in 2022

Going into 2022 it’s time to start thinking smarter, not harder, when it comes to your business, and F1 Solutions can help you do that when it comes to your IT department. We are the managed IT service provider you need to be able to focus on other areas of your business, and take it to the next level.