Here are the latest insights into CMMC (2.0):
For most of this year, the DoD, CMMC-AB, and defense contractors were all holding their breaths while the internal investigation ran its course:
- Would the CMMC-AB be dissolved?
- Would the DoD take over all cybersecurity assessments themselves?
- Would manufacturing equipment be exempted?
- Would the full implementation timeline be pushed back another three years due to delays?
- Would the requirements go back to the legally-grounded NIST SP 800-171 control set?
- Would small businesses be exempted?
- Would the DoD allow risk-acceptance and a less-than-perfect assessment?
- Would CMMC be cancelled completely?
We started getting answers last week:
- No, the AB will not be dissolved.
- The DoD only wants to assess the most critical programs themselves (less than 1% of total). The majority of assessments will still be done by the private sector.
- The interim timeline is changing, but the full enforcement date is still around 2027.
- The requirements go back to the legally-grounded NIST SP 800-171 control set.
- Small businesses are not exempt.
- Risk acceptance and less-than-perfection is allowed but will be managed closely (you will need to convince the DoD that it is a good idea, not just your own execs – and you will need to have a solid plan to fix the problems.
- No, the CMMC is not cancelled.
Ironically, although the DoD finally released their results and upheld the program, one small statement in CMMC 2.0 is making everyone crazy – that not all contracts with CUI will require independent assessment.
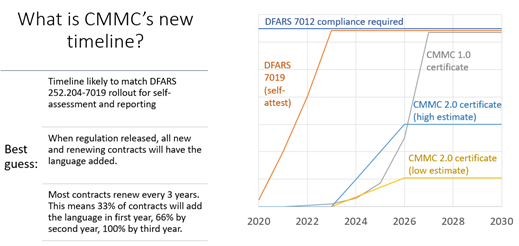
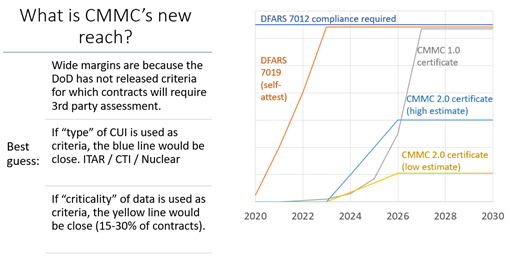
Here are my estimates for the new timeline and reach of CMMC 2.0. Note that DFARS 252.204-7012 (basically identical to CMMC now, except without the third-party assessment) is still in effect and it requires full cybersecurity protection of CUI.
Q: My company has “critical” contracts (weapons, aerospace, defense readiness, etc). What changes for us?
You (probably) will still need a CMMC assessment to win contracts between 2024 and 2027.
The three things that really changed for you are: Removal of high-cost requirements, documentation returned to “normal” levels, and allowance for imperfection.
Removal of high-cost requirements:
Email sandboxing, DNS filtering, central log aggregation server, and security assessment of internally developed programs have been removed. These were the high dollar technical requirements added in the “Delta 20” of CMMC 1.0.
Cybersecurity experts will unanimously agree that each of these items greatly reduce risk from cyber-attack, especially the sandboxing and DNS filtering solutions. So please consider carefully before you cancel them – but you won’t fail an audit if you do.
Documentation returned to “normal” levels
CMMC 1.0 tried to merge cybersecurity with CMMI level 3+ process maturity across the entire IT organization. Very few people understood what a bad idea this was since the only “CMMC assessments” were being conducted against C3PAOs. The C3PAOs found out that in order to pass CMMC “process maturity”, they had to write 300-500+ pages of brand new, step by step, flawless procedures. These were procedures for each of the 382 Assessment Objectives in CMMC. Not procedures that are repeatedly performed by an IT department. To pass, everyone supporting IT and the assessor themselves had to perform the procedure without any missing steps. For example, one C3PAO had a MAJOR finding because a single link in their procedures failed to open. It turned out that the problem was on the assessor’s side, or they would have failed.
This level of process maturity expectations caused the majority of C3PAOs to fail their assessment even though they had special training, experienced cybersecurity staff, and dedication to CMMC. The DoD realized that if they kept this requirement, defense contractors would fail at massive rates (they don’t have the advantages of C3PAOs). I suspect the DoD also realized that requiring every company to hire full time process specialists to pass CMMC was not a value-add.
So now, documentation requirements go back to industry standards and government standards: have policies; have procedures to perform your activities. These documents will be referenced as evidence in your assessment, but only as the documentation relates to the CMMC requirements. For example, you will want to “define” things like your password policy using policy or procedure documents. In short – you still need policy and procedure, but it is now just the policy and procedure standards that the government uses themselves.
Allowance for imperfection
With the CMMC 2.0 changes, you are much more likely to pass your third-party assessment on the first try. The DoD will allow Plan of Action & Milestones to give companies time to resolve problems, rather than requiring perfection in order to get a CMMC certificate.
The DoD does not actually know what the process will look like yet. So, they can’t give details. But the initial concepts are these:
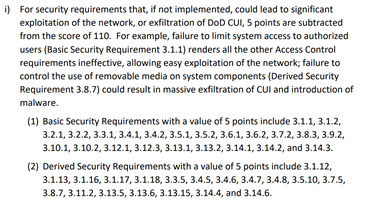
- Some CMMC requirements will be mandatory. Most likely the items scored “5”, plus the System Security Plan. (Reference the NIST SP 800-171 Assessment Methodology for full list)
- The plan to fix an issue must have an ambitious completion date. The DoD mentioned 6 months as an example.
- The timelines must be met. This probably means re-assessment or submission of progress reports every few months.
Q: My company has “non-critical” contracts (building maintenance, back-office support). What changes for us?
All the above changes apply to you as well – you still need to implement all the cybersecurity requirements to protect that CUI. But you (probably) will not need to get a CMMC certification to win contracts.
The DoD will instead monitor your cybersecurity stance by requiring self-assessments and reporting of the results. My guess is that they will also require you to submit your Plan of Action & Milestones to the DoD for review over time, but this is not defined yet.
How will CMMC be scoped?
The Certified CMMC Professional courses include a scoping module. Unfortunately, this module does not clarify the questions about scope, boundaries, and inter-connected systems that technical staff have. It instead discusses organizational scoping – understanding the people that are involved to support cybersecurity.
Organizational scoping is very important and is applicable to perhaps half of the requirements (the ones that are manually performed). But it doesn’t address what to do when a single department asks for assessment while using an information system that spans a larger company.
The best scoping guidance at this time is still what is found in the DFARS 252.204-7012 (this is also the scoping guidance that the DoD has been using for their assessments):
“Covered contractor information system” means an unclassified information system that is owned, or operated by or for, a contractor and that processes, stores, or transmits covered defense information.”
“Covered defense information” means unclassified controlled technical information or other information, as described in the Controlled Unclassified Information (CUI) Registry at http://www.archives.gov/cui/registry/category-list.html, that requires safeguarding or dissemination controls pursuant to and consistent with law, regulations, and Governmentwide policies, and is—
(1) Marked or otherwise identified in the contract, task order, or delivery order and provided to the contractor by or on behalf of DoD in support of the performance of the contract; or
(2) Collected, developed, received, transmitted, used, or stored by or on behalf of the contractor in support of the performance of the contract.”
Action statement from DFARS 252.204-7012: “The Contractor shall provide adequate security on all covered contractor information systems.”
This means that the assessment focuses on systems that have CUI. Every requirement is checked for those systems. Other systems are reviewed only if the requirement calls them out.
For example, your Mission Department workstations have CUI on them. Every requirement for audit logging, antivirus, account control, least privilege, warning banners, etc, is reviewed on the Mission Department workstations. Your directory servers (account management) are assessed to make sure they are limiting access appropriately. Your firewall is assessed to verify that it denies traffic by default. But other workstations in the company (that have no access to CUI) are not assessed.
It is possible that the DoD will release different scoping guidance, but there is a strong precedent for the above. This scope also makes an assessment reasonable – if other scopes are used, an assessment would easily apply to 5x the number of systems.
When should we expect more information?
The DoD stated that they plan to release more information about the CMMC program over the next “several weeks” – this translates to sometime before the end of 2021.
New information will be posted at the DoD’s CMMC website: https://www.acq.osd.mil/cmmc/
For CMMC Consulting and guidance, contact F1 Solutions located in Huntsville, Alabama today. No one is an expert in CMMC right now since the program is still so new and being developed. However, F1 is making huge efforts to stay up on the latest information coming from the CMMC group and the accreditation board. Stay tuned for more updates coming soon.