Colonial Pipeline was hacked by the Eastern European cybercriminal gang DarkSide on May 7, 2021. The hackers encrypted Colonial Pipeline's data and demanded ransom in exchange for decryption This compelled Colonial Pipeline’s CEO to pay out over $4.4 million in Bitcoin a few days after the hack, despite the conventional belief that one should not give in to ransomware operators in hopes of retrieving data.
Blog
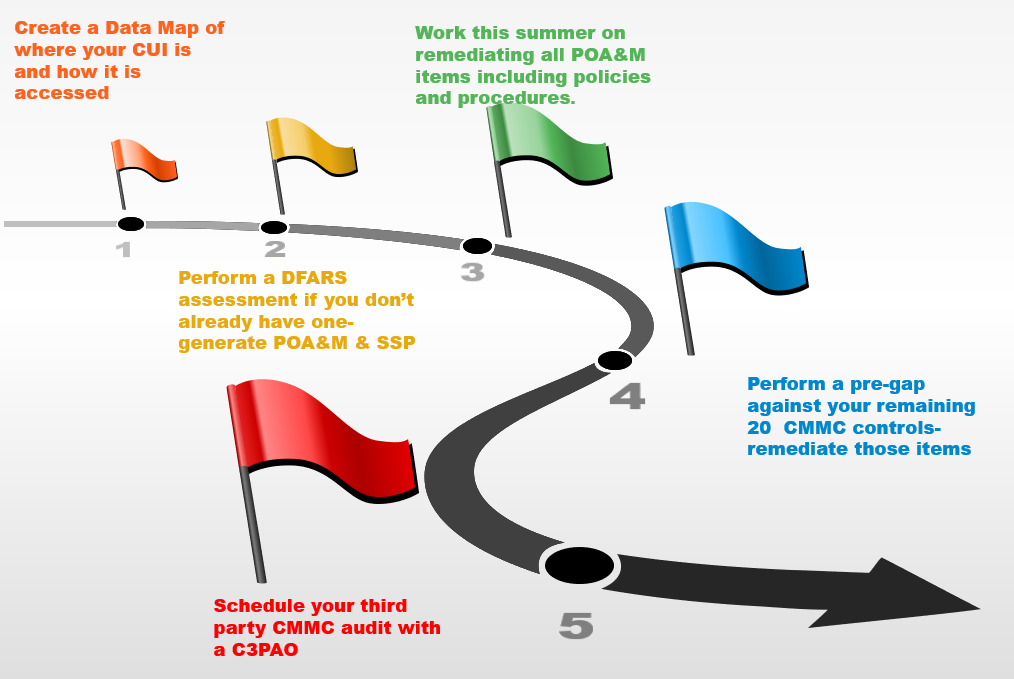
What are the CMMC (Cyber Security Maturity Model Certification) Levels
Registered Practitioner Organization’s (RPO) versus Certified Third-Party Organization’s (C3PAO) What is the difference?

You now know about the Cybersecurity Maturity Model Certification (CMMC) but let ‘s discuss a little about the different types of people and groups associated within this ecosystem. We are going to break these individuals down into two groups. The organizations registered through the CMMC AB , and the individual people registered through the program (for now we are leaving out other ancillary categories).
Organization
C3PAO’s (Certified Third-Party Auditing Organizations)
This is a company that has met all CMMC certification criteria and submitted the requisite documents to the CMMC AB to qualify as an organization that can contract directly with a Government Contractor for the purpose of either a pre-assessment or a certified third-party assessment.
A NON-Official Update on Where CMMC (Cybersecurity Maturity Model Certification) Seems to be as of Today
4 Simple ways to better manage your work email

North Alabama businesses are back in full swing, which means workers are once again receiving and sending countless emails every day. Emails have become such a necessity in today’s work environment that failing to manage them appropriately can lead to decreased productivity and increased risk of cyberattacks.
Frequently asked questions about the CMMC
The US Department of Defense (DoD) recently released new rules about data protection that its contractors need to abide by. Due to the sensitive nature of the data DoD vendors deal with, as well as the increasing prevalence of cybercrimes, it’s imperative that the agency maintains full control over its information assets.
Why every business should have cyber insurance coverage

Cybercrime is on such a rise that businesses are scrambling to protect their operations in all manners possible. For one, Madison County in Alabama has experienced an uptick in phishing and wire transfer scams in the past five years. So, it’s vital to not only implement solutions that minimize the risk of attack, but also measures that will help manage the financial risk of such threats.
Encryption
Cybersecurity Maturity Model Certification (CMMC)

The new CMMC model was created by The Department of Defense under the Secretary of State. This program was designed in order to keep Controlled Unclassified Information (CUI) out of the hands of government officials who are not DFARS compliant.
DFARS (Defense Federal Acquisition Regulation Supplement) and CMMC accreditation will now be required for all government contractors and suppliers with CUI access.
Network Security

A security breach can be detrimental to your business. Small businesses are being targeted more than ever by hackers, phishing attacks, and viruses. Your data can be stolen, ultimately paralyzing your operations. Don’t wait until this happens! Contact F1 Solutions and our skilled tech experts can assess your network and identify any weaknesses.